The RMF steps include. Tap card to see definition.
 Issa Nova Sig Risk Management Framework Life Boat
Issa Nova Sig Risk Management Framework Life Boat
Authorize and Step 6.

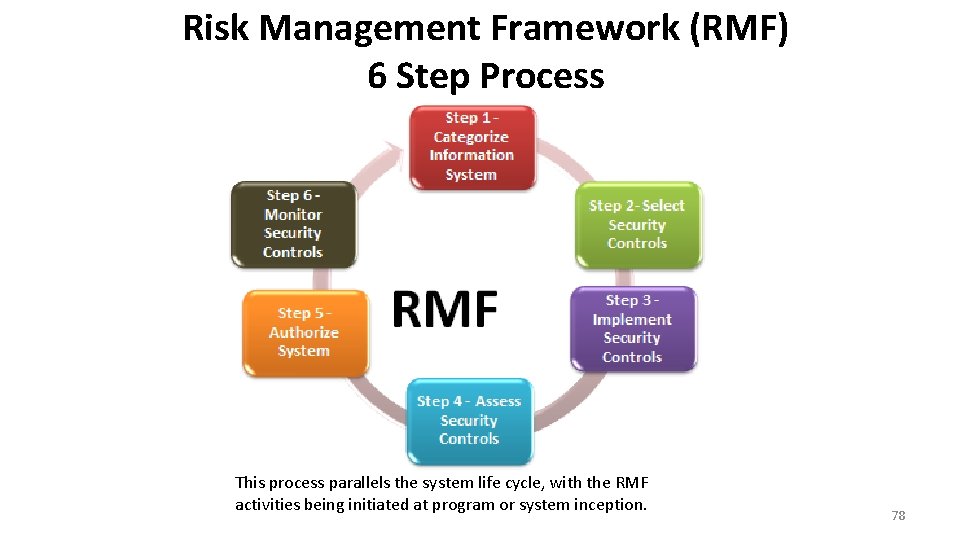
6 steps of rmf. The RMF is a culmination of multiple special publications SP produced by the National Institute for Standards and Technology NIST - as well see below the steps of the NIST RMF split into 6 categories Step 1. An example of the Security Categorization for an Information Type of PHI is provided. - are appropriately marked protected and handled - used to help satisfy OMB Circular A-130 reporting requirements - used to determine reauthorization need - occurs at appropriate intervals.
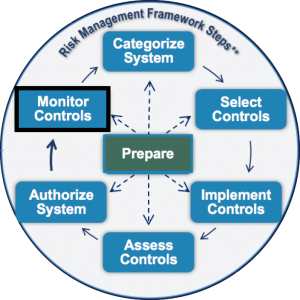
1 Categorize System Select Security Controls Implement Security Controls Assess Security Controls Authorize System and. Categorize the information system and the information processed stored and transmitted by that system based on an impact analysis. RMF Step 1 Categorize Information System.
The course modules will prepare the student to for their role and. All information that is processed stored and transmitted on the system must be categorized using the new security objectives and impact levels. Risk Management Framework RMF Step 6.
Tap card to see definition. NIST Risk Management Framework 3. Each step in the process is discussed at a high level.
The RMF breaks down these objectives into six interconnected but separate stages. This blog post is a transcript of Alpine Securitys Risk Management Framework RMF Overview video which covers an overview of RMF as defined by NIST 800-37r2. Categorize the system and the information that is processed stored and transmitted by the system.
Define Risk Management Framework RMF Assessment and Authorization AA process and identify its purpose and timeline Identify the legal regulatory and contractual requirements that govern the RMF AA process Identify and define Defense Counterintelligence and Security Agency DCSA. Tap again to see term. Since the other steps depend on this being done correctly it is important to identify all policies procedures and information types.
Monitor Security Controls CS10716. This course covers the final step of the Risk Management Framework process. Click again to see term.
The report criteria and use in Step 6 of the RMF includes all but which one of the following. At the broadest level RMF requires companies to identify which system and data risks they are exposed to and implement reasonable measures to mitigate them. System categorization is the first step in the six steps to RMF implementation.
Categorize Identify Step 2. This step is critical in maintaining an effective security posture and accreditation status. FISMA Background About the RMF Prepare Step Categorize Step Select Step Implement Step Assess Step Authorize Step Monitor Step SP 800-53 Controls Release Search Downloads Control Overlay Repository Overlay Overview SCOR Submission Process SCOR Contact RMF Introductory Course RMF Email List Meet the RMF Team.
The 6 Risk Management Framework RMF Steps. Click card to see definition. Monitor uniquely lend themselves to a given NIST special publication ie.
Six steps in the RMF at the system level NIST Special Publication 800-37 Guide for Applying the Risk Management Framework. Vested party is identified. Click card to see definition.
RMF Step 2Select Security Controls. The RMF process parallels the defense acquisition process from initiation and consists of six 6 steps. The Six Steps of the Risk Management Framework RMF The RMF consists of six steps to help an organization select the appropriate security controls to protect against resource asset and operational risk.